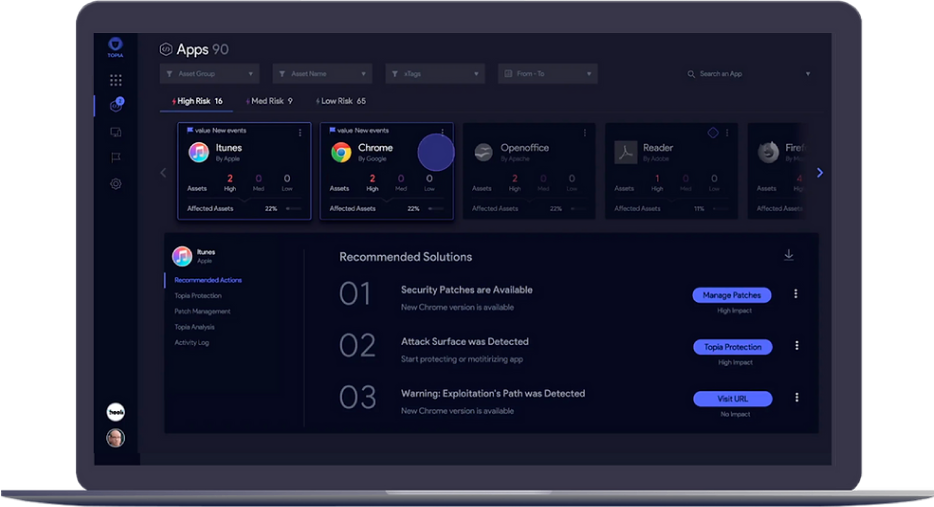
You Can Count On vRx To Carefully Scan A Range Of Assets
These include:
Network-based security scans that identify potential security attacks and exposed systems on both wired and wireless networks

Network-based Scans
In-depth scanning of servers or other network hosts to locate and identify vulnerabilities as well as to provide visibility into the configuration settings and patch history of these hosts

Host-based Scans
Identifying rogue access points and verifying that a company's Wi-Fi network is configured correctly using wireless scans of the network

Wireless Scans of the Wi-Fi Network
A scan of the application to detect known software vulnerabilities and incorrect configurations in the network or web application

Application Scans
Analyzing databases to identify weak points and prevent malicious attacks