Benefits of Pentesting
Your systems and software were designed to eradicate dangerous security vulnerabilities. A pen test provides insights into how effectively they are at achieving this goal.
Here are some possible benefits of pentesting:
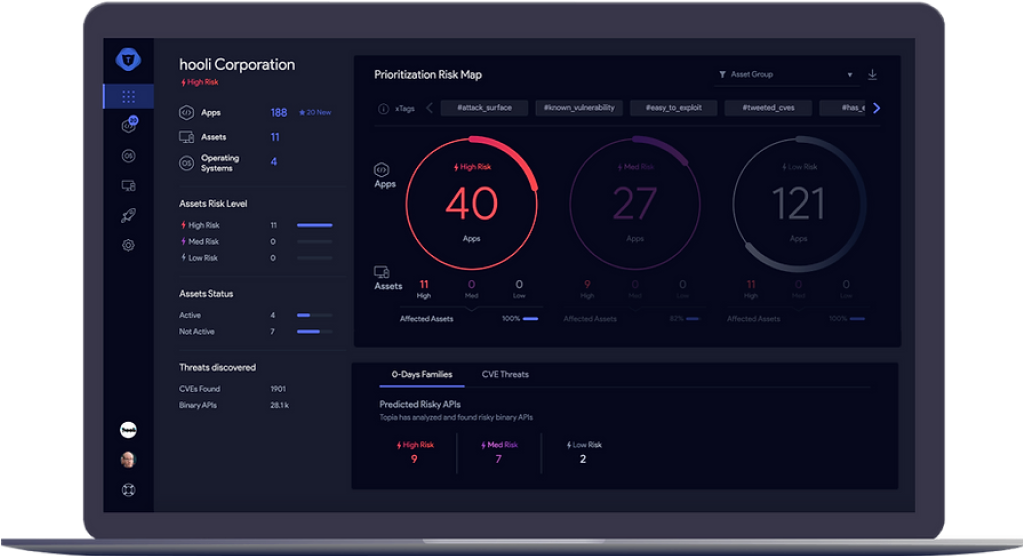
Pentesting provides a goal perspective that discloses blind spots, giving you the visibility into safety gaps that internal IT teams may miss because of unfamiliarity or lack of expertise with the sophisticated threats

Gain visibility of safety gaps
Recognize and mitigate security vulnerabilities in your IT environment to minimize the attack surface for the latest and advanced threats

Minimize attack surface
You can prioritize your security budgets and save money in the long term by avoiding wasteful expenditures on the comprehensive security landscape

Prioritize security budgets
Make sure you test your investments in your cybersecurity technology and tools to determine if any gaps or vulnerabilities exist and whether they can help you prevent a sophisticated attack on your company systems and networks