Benefits of our Vulnerability Management Software
Our vulnerability management system offers the following benefits:
It is essential to identify these flaws in application to protect the entire asset and business information. We help you ensure that these issues are assessed and prioritized according to their severity. This assessment contributes to resolving the flaws in IT assets and protecting them from cyber-attacks, resulting in security breaches.

Enhanced Security
Constantly keeping an eye on your vulnerabilities helps you save loads of time. If your environment is not monitored continuously, you may experience a breach when you least expect it and aren’t prepared for it. This can end up costing you several thousand dollars and hours of labor. Thus, frequent and rigorous monitoring can help you detect risks and quickly fix them.

Time-Saving
Vulnerability management looks deep into the entire process—not just a particular area. It starts with the vulnerability management team pointing out the risks and continues even after the threat is diminished.

Improved Infrastructure Security
vRx's round-the-clock, comprehensive security supervision lets you breathe easier knowing your sensitive data and apps are secure. Advanced detection and prevention capabilities and flexible deployment models make it easy for you to analyze, detect and deter threats in real-time. If you need intelligent, layered security, vRx can help you.


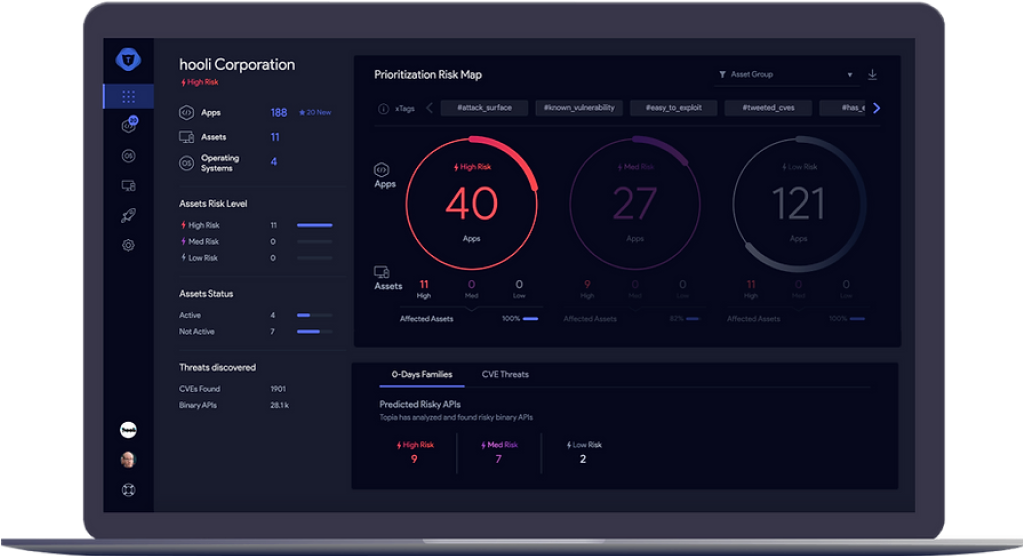
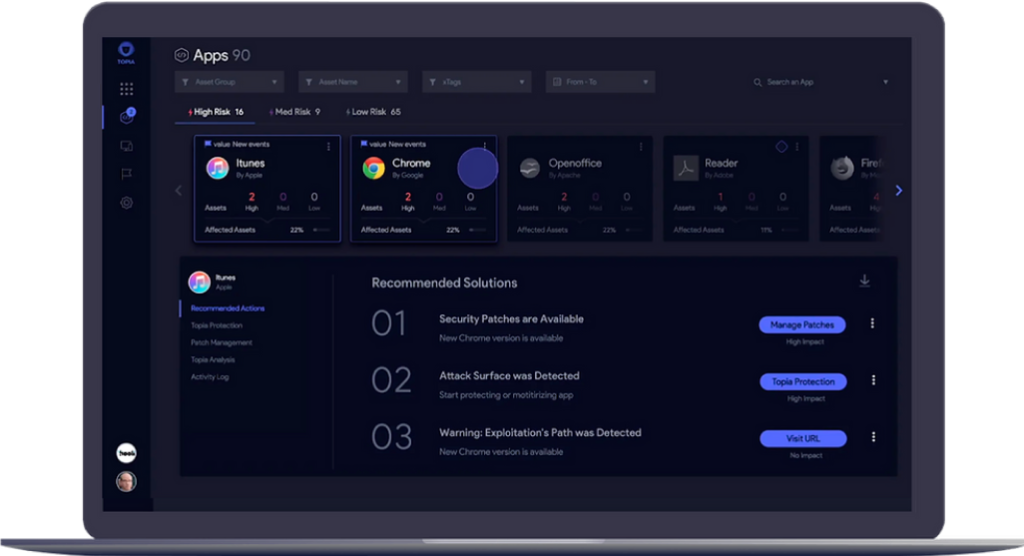
 Assess
Assess